 If the word “exfiltration” doesn’t fill you with horror, it should. If you’re not crossing yourself and knocking on wood every time you hear it, you need to learn a little more about exfiltration and what you can do to combat its threat to individuals and businesses the world wide web over. But never fear, this blog is here to tell you everything you need to know…
If the word “exfiltration” doesn’t fill you with horror, it should. If you’re not crossing yourself and knocking on wood every time you hear it, you need to learn a little more about exfiltration and what you can do to combat its threat to individuals and businesses the world wide web over. But never fear, this blog is here to tell you everything you need to know…
What is exfiltration?
Exfiltration is a term used to describe an unauthorised file transfer or an alternative bulk data transfer which allows the baddies of the internet to weevil into your system and access your confidential information, even through a secured network. This can cause a catastrophic data leak and security breach which could spell disaster for your business and your customers. Those are the basics. I’ll be explaining a little more about how exfiltration works later. But first…
How do you prevent exfiltration?
Preventing (and even detecting) exfiltration can be a difficult business and you’ll need to defend your system on three distinct fronts by using:
1. Managed file transfer (MFT)
- There are a number of specialist providers out there who offer strong, secure managed file transfer services (I’d recommend taking a look at taking a look at Thruinc.com if you’re looking for a FTP alternative to roll MFT out across your business).
- MFT is a crucial weapon you can use to defend against exfiltration as it minimises how exposed your system is to malicious activity. By ensuring all of your files are transferred in a carefully managed and monitored way, you can reduce opportunities for exfiltration (think about it like closing chinks in your armour) by giving hackers less sensitive data to latch onto. It’ll also allow you to set up egress filtering (more about that later!).
2. Egress filtering
- Another essential string to your defensive bow, egress filtering will allow you to prevent the majority of your resources from being turned into exfiltration servers. Egress filtering stops all unmonitored, free access from all internal machines to any external server, keeping you nice and safe.
Malware detection
The final part of your anti-exfiltration armoury has to be powerful anti-virus software (with cutting edge malware detection) which runs on all possible devices used within your business. You’ll find a guide to choosing the best software for a small business on the (frankly indispensable) TechRadar website. The better the software and the more widely used it is across your business, the better chance you stand of getting in the way of the collection applications hackers use to get hold of your sensitive information
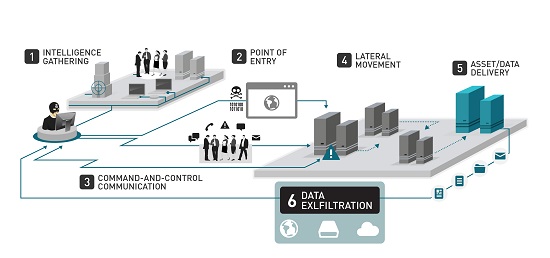
How exfiltration works (in a nutshell)
Yet another great weapon you have against the scourge that is exfiltration is knowledge. Knowledge is power and the better you understand your enemy, the more effectively you can defend against it. But before I start sounding like an extract from The Art of War, I’ve got some explaining to do…
- Where it comes from
The first contact your business will likely have with hackers intent on exfiltration will affect your business’s “endpoints”. These can be pretty much any device which is susceptible to malware. We’re talking about point of sale devices, smartphones, laptops, tablets, desktop PCs, database servers – you name it. Malware which gets installed on these devices will then steal sensitive data. - It’s exfiltration time
Armed with this sensitive data, the malware will then transfer its findings to the exfiltration server usually in bulk in the form of a bundle of data using an in-built protocol like Microsoft file shares. - The endgame
In the final, critical step, the exfiltration server then “pushes” its stolen file full of your important, private data out to the hacker’s external server. At this point, the worst has happened and it’s too late to get your data back. It’s all over.
Why is it so dangerous?
Aside from the obvious fact that exfiltration leaves your data open to hackers, this technique is very nasty as very few businesses take the time to look at what is run-of-the-mill web traffic and what is (potentially dangerous) external traffic. That means that the majority of companies are totally blind to exfiltration when it happens and the practice can mean hackers continue to access your system without your knowledge over the long term. According to one study, it took 156 days for breaches to be detected. For an example of nasty exfiltration in action, take a look at what happened to Target and start getting yourself protected, pronto.
Does your business take measures to protect against exfiltration? Are your IT team up to speed? Have you been affected by this practice yourself? Share your thoughts and experiences with readers below.


